Update – January 19, 2015
After posting the last update a week ago, I spent more time rooting around the Microsoft Web site, and ended up in a relatively painful 45-minute chat session with a Microsoft “Licensing Specialist.” A large portion of that time was spent just trying to get said Licensing Specialist to understand the question I was asking. Ultimately, I had to give up on my attempt to get an answer as to why Microsoft still had a live link to a Volume License Brief that appeared to be out of date and that apparently contained information that was no longer valid…because the Licensing Specialist couldn’t get to the document in question. According to her, when she clicked on the link below, she received an error message stating that the document had been removed from the Microsoft Web site. As I write this update, the link to the 2009 Volume License Brief is still live, and I just verified that the document is still there. I will leave it to you to figure out why I can still get to it but she couldn’t. She offered to have a Microsoft manager call me the next day. It’s been a week now, and I have yet to receive that call. (It’s possible that the manager attempted to call me, but, if so, did not leave a voice mail message.)
In the absence of any other information at this point, my best advice is to assume that this Volume License Brief supersedes the information in the earlier one (even though the earlier one is still available on Microsoft’s Web site), and that, to be on the safe side, you should insure that, if you are accessing Office applications via RDS, the edition and version on your RDS server(s) match the licenses you have for your client devices.
…end January 19 update…
Update – January 12, 2015
A few days ago, Markus challenged my statement (see comment below) that it was permissible to access Office Standard via Remote Desktop Services if your client was licensed for Office Pro Plus, and that it was also permissible to access an older version (e.g., Office 2010 Pro Plus) via Remote Desktop Services if your client was licensed for a newer version (e.g., Office 2013 Pro Plus). I can state definitively that this was the case, as recently as November, 2009. This Microsoft Volume License Brief, originally published in 2007, and updated in November of 2009, contained the following graphic (click to enlarge):
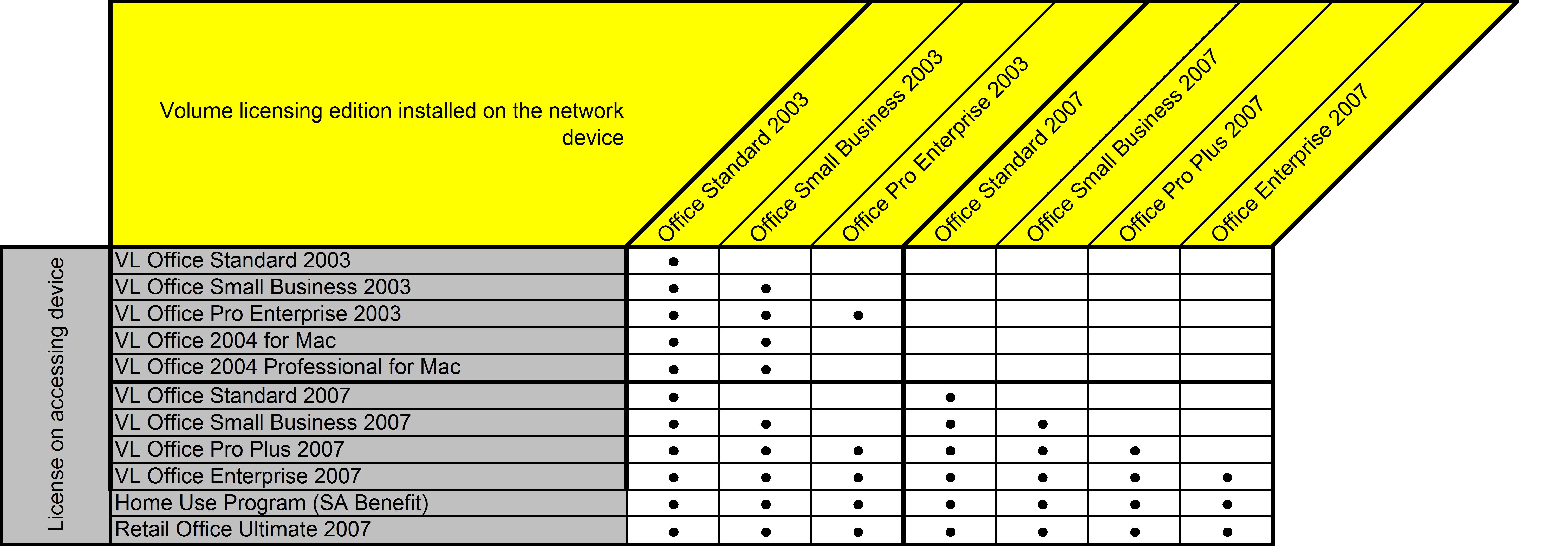
This graphic clearly shows that it was permissible to access Office Standard from a client device licensed with Office Pro Plus, and that it was permissible to access an older version of Office from a client device licensed with a newer version. However, a later Volume License Brief suggests that this may have changed. I am attempting to get clarification from Microsoft, and will update this post again as I get more information.
…end Jan. 12 update…
Judging from the questions we continue to be asked, lots of people are confused about how to license the Microsoft Office Suite if you are accessing it via Microsoft’s Remote Desktop Services (a.k.a. Terminal Services) and/or Citrix XenApp. Hopefully, this will help clear up the confusion. We’ve also updated this post to include information about how to license the applications in a Cloud hosting environment.
First of all, it is important to keep in mind that desktop applications such as the Office Suite are licensed per device, not per user. According to the latest Microsoft “Product Use Rights” document dated April, 2014, a “Licensed Device” is “the single physical hardware system to which a license is assigned.”
That begs the question of what “assigned” means, and the answer – particularly for devices like thin clients, where you couldn’t install the application locally if you wanted to – is that you are on the honor system. You decide, in the privacy of your own conscience, which licenses you are assigning to which devices – with the caveat that, if you’re ever audited, you’d better be able to produce a license for every device people are using to run Office apps. You can reassign a license from one device to another, but not more often than every 90 days, unless it’s due to permanent hardware failure.
Once you’ve assigned each license you acquire to a device, you have the following rights (again quoting from the Product Use Rights document, with my commentary in italics):
- You may install the software on the Licensed Device and a network Server.
- Unless you license the software as an Enterprise Product or on a company-wide basis, you may also install the software on a single portable device. That would cover a user who, for example, had both a desktop PC and a notebook PC.
- Each license permits only one user to access and use the software at a time. So, technically, it would be a license violation for someone else to run Office on your desktop PC while you’re in a hotel somewhere running it on your “portable device.”
- Local use of the software running on the Licensed Device is permitted for any user. So it’s OK to let someone else use your desktop PC to run Office, as long as you’re not simultaneously running it on your “portable device.”
- Local use of the software running on a portable device is permitted for the primary user of the Licensed Device. So, technically, it would be a license violation for you to let someone else run Office on your “portable device” under any circumstances.
- Remote use of the software running on the Licensed Device is permitted for the primary user of that device from any device or for any other user from another Licensed Device. So if your Licensed Device is your desktop PC, it’s OK for you to use GoToMyPC or some similar remote access method to access and run that copy of Office, using whatever kind of client device you want – including, say, an iPad. However, any other user could not remotely access your desktop PC to run that copy of Office unless they were doing so from another Licensed Device.
- And now the most important point relative to the subject at hand… Remote use of the software running on a network Server is permitted for any user from a Licensed Device. A Remote Desktop Server falls under the definition of a “network Server.” So any user who is accessing Office via Remote Desktop Services must be doing so from a Licensed Device.
In other words, if you can walk up to a device and use it to access a Remote Desktop Server and run Office, you must have an Office license for that device. It doesn’t matter whether that device is a PC or laptop that has the Office bits installed on its local hard drive, or whether it is a thin client device that only knows how to connect to a XenApp server, you need to have “assigned” a license to that device.
It’s also important to note that all of the above came from the Product Use Rights document for Microsoft Volume Licenses. You do not, never have had, and probably never will have the right to access Office on an RDS or XenApp server from a device that has an OEM Office license installed on it. If your PC or laptop came from the manufacturer with Office pre-installed on it, then you have an OEM license, and you do not have “network storage and use” rights. There is an excellent blog post over on the Microsoft SMB Community Blog that explains this in detail. Yes, it’s an old post (from July, 2005). No, the policy hasn’t changed.
Things get a bit more complicated when you move to the Cloud. For example, if you are a VQOffice® customer, and you want to run Office apps on our cloud servers, we can, of course, bundle the Office licenses into your monthly fee under our Microsoft SPLA (“Service Provider License Agreement”). But what if you already own volume licenses for Office? According to the Product Use Rights document, we can use your licenses “provided all such Servers and other devices are and remain fully dedicated to your use.” Given the highly virtualized environments of nearly all Cloud hosting providers (including us), that’s going to drive the cost of the solution up significantly unless you have enough users to justify dedicating hardware in our data center just for your use. For most small businesses, it will be less expensive to pay us for the use of our SPLA licenses than to pay us for dedicated hardware so you can use your own licenses.
What about Office 365? Office 365 is governed by a completely different use rights document – the Online Services Use Rights document. If you read through that document, you will find that, under the E3 plan for example, each user has the rights to activate the Office software on up to five devices, which is a pretty good deal. You will also find the following statement: “Each user may also use one of the five activations on a network server with the Remote Desktop Services (RDS) role enabled…” At first blush, you might think that means you could use your Office 365 E3 licenses to cover running Office apps in our Cloud hosting environment – and you would be right, provided that you’re running on dedicated hardware. So, basically, the same rules apply to Office 365 licenses as apply to volume licenses. We’d be delighted if the rest of the world added their voices to ours to try to get that policy changed.
Disclaimer: I do not work for Microsoft, nor do I define their license terms, which are subject to change, particularly when new product versions are released. I have, however, worked with them for a very long time, and had lots of discussions about what is, or is not, legal under the terms of various license models. The foregoing is my own interpretation of information that is publicly available on the Microsoft Web site – and I have helpfully provided you with links to that information. I highly recommend that, if you have any questions, you download the relevant Product Use Rights document and read it for yourself.





